DATA PROTECTION TRENDS, NEWS & BACKUP TIPS
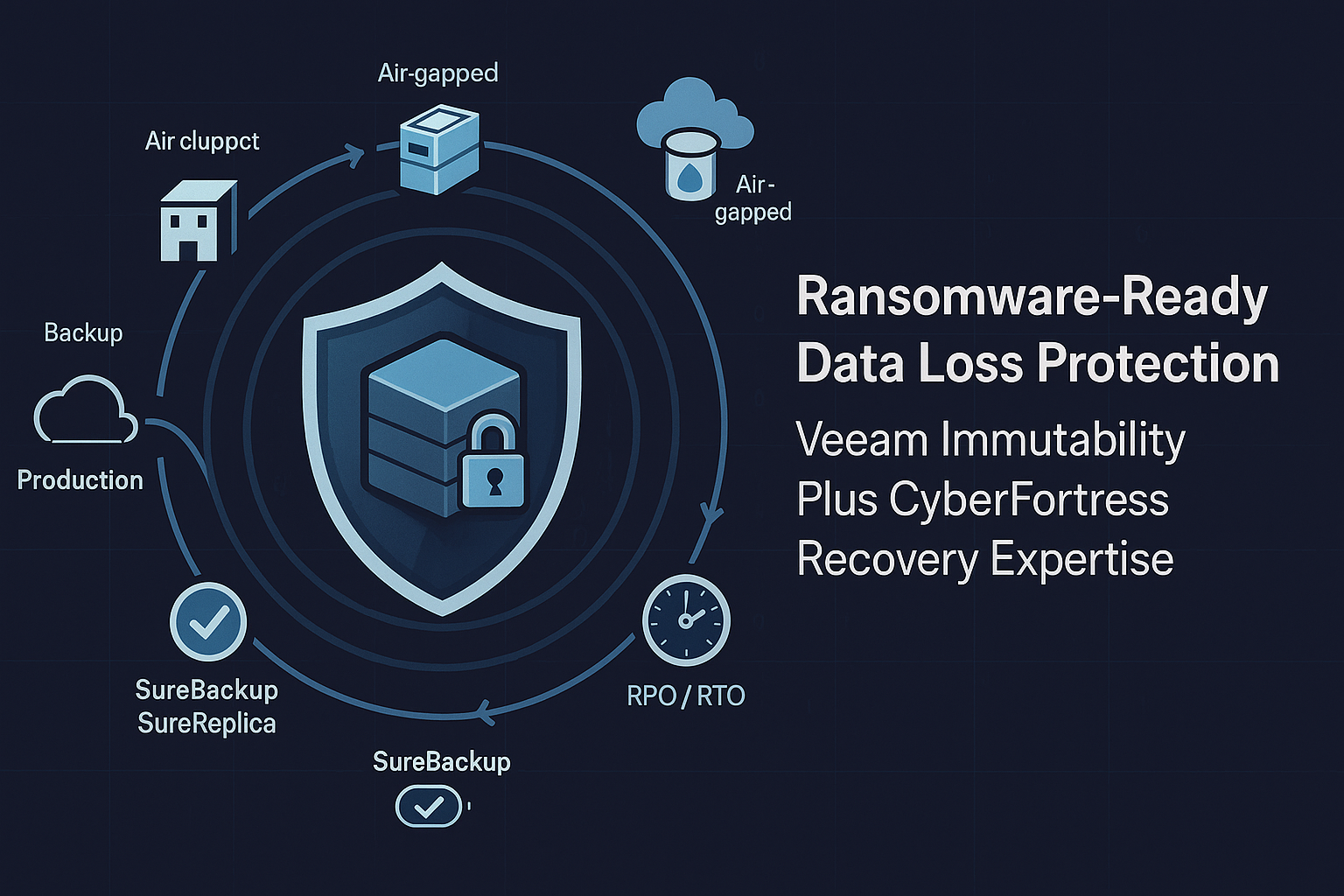
Ransomware-Ready Data Loss Protection
Evolving Ransomware Tactics and Backup Failure Points
Modern ransomware attacks are adept at not only encrypting primary data, but also seeking out and destroying backups. Attackers know that if they can eliminate recovery points, an organization is more likely to pay the ransom. Studies confirm this trend: in one survey, nearly 99 percent of recent ransomware incidents included attempts to compromise backup repositories.
Common backup failure points that leave organizations vulnerable include:
- Online-only backups: Storing backups on network-attached storage that remains online or using the same credentials as production systems. If malware gains admin access, it can encrypt or delete these backups easily.
- Lack of offsite or air-gapped copies: Keeping all backup copies on the same network or site means a single breach or disaster can wipe out everything.
- Untested backups: Backups that are not regularly verified may be incomplete or corrupted, leading to unpleasant surprises during recovery.
The impact of these weaknesses is severe. Without a viable backup, ransomware can cause total data loss or prolonged downtime. To achieve true data loss protection and ransomware protection, IT admins should close these gaps with a multi-layered defense of immutable storage, isolated backup copies, and proven recovery processes.
Building an Immutable Backup Tier with Veeam
One of the most powerful shields against ransomware is immutable backups. Immutability means a backup file is locked against changes or deletion for a defined retention period. Even a rogue admin account, or malware that hijacks admin privileges, cannot alter or purge those backup files until that timer expires. This keeps your last line of defense intact even if attackers breach your systems.
Veeam Backup & Replication makes it straightforward to implement an immutable backup tier:
- Hardened Linux Repository: Veeam’s hardened repository feature allows backups to be written to a Linux server with the filesystem’s immutability flag enabled. Once saved, backup files cannot be modified or removed by any user or process for the duration you specify. This protects backups even if an attacker gains elevated access to the repository server.
- Object Lock in Cloud Storage: Veeam integrates with object storage immutability, such as S3 Object Lock. When using Veeam’s Capacity Tier to copy backups to object storage, you can enable Object Lock so that cloud backup copies are stored in a write-once, read-many state.
By leveraging these Veeam immutability features, organizations ensure that attempts to wipe out backups fail. Veeam supports immutable repositories both on premises through the hardened repository and in the cloud through Object Lock, so you can preserve clean restore points that malware cannot touch.
Air-Gapped Backups and Offsite Copies for Ransomware Resilience
Another key to ransomware-ready data loss protection is designing air gaps and offsite redundancy into your backup strategy. An air-gapped backup is offline or otherwise isolated from your production network, so that malware cannot reach it remotely. Traditionally, tape backups provide a physical air gap. Once a tape is ejected and stored offsite, ransomware has no way to destroy the data on it. Veeam supports copying backups to tape, allowing organizations to maintain periodic archival backups that are completely offline.
For more continuous protection, Veeam’s backup copy jobs enable creating offsite backup copies to a different location or platform. This aligns with the best-practice 3-2-1 rule: keep at least three copies of your data on two different media, with one copy offsite. For example, you might keep recent backups on a local Veeam repository for quick restores, and configure a Backup Copy job to send those backups to a secure cloud repository or secondary data center. Veeam can automate moving backup copies offsite as part of the backup workflow.
Equally important is logical isolation. The offsite backups should use separate credentials and ideally live in an environment not accessible from the primary domain. This way, even if an attacker compromises your production network, they cannot easily reach your secondary backup copies. Offsite cloud backups through services like CyberFortress BaaS are stored in a separate, secure environment, adding an extra layer of isolation. The combination of offsite, air-gapped backups and immutability means that even a widespread ransomware attack cannot eliminate your ability to recover. At least one pristine copy of your data will survive.
Automated Backup Verification with SureBackup and SureReplica
Having backups is one thing. Knowing those backups will actually work for recovery is another. This is where automated verification comes in, and Veeam provides built-in tools to ensure recoverability. SureBackup allows you to automatically start VMs from your backup files in an isolated Virtual Lab and run health checks. For example, you can schedule a SureBackup job nightly or weekly to boot critical server backups and verify that they power on, the OS responds to heartbeats and pings, and applications start correctly. Veeam can also execute custom scripts inside the sandboxed VMs to confirm that databases, websites, or other services are functional. If any backup is incomplete or corrupted, these automated tests will flag it early, long before you ever need that backup in a real emergency.
Similarly, SureReplica performs recovery verification for VM replicas. It validates that your replicas are usable by periodically powering them on in the isolated lab and running the same checks.
Regularly running these verification jobs gives IT teams confidence in disaster recovery readiness. It is essentially a fire drill for your data center. You prove that you can restore systems from backup, rather than just assuming it. The process also generates documentation and logs that you can use as compliance evidence for DR testing requirements. A helpful mantra applies here: never just trust backups. Always verify they are secure and functional through routine test restores.
CyberFortress Recovery Services: Minimizing Downtime
Even with strong tools like Veeam in place, expert support during a crisis can drastically shorten downtime. CyberFortress brings recovery expertise to complement your immutable, air-gapped strategy. CyberFortress offers fully managed BaaS and DRaaS powered by Veeam, which means our team handles the complex tasks of data protection and will be there to assist if ransomware strikes. Key services include:
- Incident response support: 24×7 assistance to contain the attack, identify the scope, and formulate a recovery plan.
- Guided recovery and orchestration: Engineers who specialize in Veeam recovery help spin up critical servers from backups in our cloud or yours, leveraging instant recovery and replication to get operations running again. In one real-world case, CyberFortress spun up 200 to 300 customer servers from backups within a week to meet an urgent full-site recovery need.
- Scheduled restore tests: Regular restore testing, such as quarterly DR drills or monthly sample restores, validates backups and recovery runbooks. We handle logistics and automation, then provide detailed reports.
- Compliance and audit reporting: Documented tests and backup status checks produce audit-ready evidence for frameworks such as ISO 27001, HIPAA, and SOC 2.
By partnering with CyberFortress, you gain an extension of your IT team focused on data resilience. A managed service can handle the heavy lifting of setting up offsite immutable backups, monitoring backup jobs around the clock, and assisting with recovery when needed, all while maintaining your backups in a separate environment that isolates them from your production network. This not only offloads routine work, it also adds security: backups maintained by CyberFortress reside in a separate domain, insulating them from threats on your primary network. Our broad experience with ransomware recovery across many clients helps you avoid pitfalls and accelerate time to restore.
From Attack to Clean Restore: A Ransomware Recovery Scenario
Late one night, a company’s servers begin getting encrypted by ransomware. Security alerts go off, but the attack spreads rapidly across file shares and critical VMs. Fortunately, this company was prepared. Recent backups were replicated offsite to a hardened Linux repository in a CyberFortress data center with immutability enabled. Even as the ransomware attempted to delete or encrypt backup files, those copies held firm, and the malware could not alter the write-protected restore points. The IT team had isolated these backups from the domain, so the attacker had no direct network path to reach them.
By morning, IT invokes the incident response plan with CyberFortress. Infected systems are taken offline and replaced with clean hardware or VMs. The team identifies the last known clean backups from just hours before the attack. Thanks to Veeam’s instant recovery features, critical VMs are booted directly from immutable backup copies, bringing key services back online within a few hours. Additional servers are restored in parallel to a sandbox environment using SureBackup to ensure no dormant malware comes over during recovery. Within the same day, the business is largely back on its feet, without paying a ransom.
This scenario highlights the value of a ransomware-ready data protection strategy. Immutable, air-gapped backups preserved recovery options. Thorough testing prevented surprises during restoration. Expert recovery support from CyberFortress kept the process smooth under pressure.
Conclusion: Resilience Through Technology and Expertise
Ransomware is an ever-present threat, but it does not have to paralyze your organization. By combining Veeam’s data protection technology, including immutability, automated testing, and fast recovery, with CyberFortress services and ransomware protection expertise, you can reach a level of resilience where cybercriminals do not win. An attack might slow you down for a day, but it will not put your data or business in jeopardy.
Do not wait for an attack to reveal weaknesses in your backup strategy. Take a proactive stance and review your preparedness regularly. Schedule a resilience review with CyberFortress to assess your current backup and recovery posture. Our experts will help identify gaps, from confirming that backups are truly immutable and air gapped to validating recovery times, and build a plan to fortify your defenses. With ransomware-ready data loss protection in place, you can face cyber threats with confidence knowing your data is safe, your backups will hold, and your business can bounce back in hours instead of weeks.