Jonah May
Data protection experts discussing insights over Veeam’s Ransomware Trends report in how to “be prepared” when it comes to the topic of ransomware and disaster recovery
Real world ransomware survey outcomes from cybersecurity and data backup teams regarding their cybersecurity preparedness was examined
Why, now more than ever, it’s important to have a reliable data backup strategy and how to implement one for effective data recovery and operational restoration
I recently had the privilege of hosting a webinar with Jason Buffington, Vice President of Market Strategy at Veeam. As a lover of Scouting and its motto of “be prepared”, I couldn’t agree more with the importance of being ready when it comes to ransomware and disaster recovery.
During the webinar, Jason and I delved into Veeam’s 2023 Ransomware Trends report and explored trends and insights on how to stay prepared in the face of cyber threats. On this blog, I will cover the insights from the webinar.
But you may wonder: Why is the Ransomware Trends report so valuable?
Veeam’s research project surveyed 1,200 organizations that had experienced at least one cyber attack in 2022. The participants included various roles involved in preventing or mitigating cyber events, such as CISOs, backup admins, IT operations personnel, and security professionals. As I read through the report, it made me wonder, are in any of these crucial roles? If you are, I highly recommend taking the time to read the report if you haven’t already.
The 2023 ransomware trends report presents real and up-to-date data from organizations of different sizes, offering a wide-ranging perspective on the cybersecurity challenges faced across various industries. Its purpose is to equip you with valuable insights on how to recover after a ransomware attack or even prevent such an attack by ensuring preparedness across all departments within your company.
One of the ways we aimed to enhance participants’ understanding of current cyber threats was through our webinar ” Be Prepared, Never Pay Ransom, Recover Instead”. Jason and I took this opportunity to delve deeper into the critical issues that hinder teams from being adequately prepared for cybersecurity threats and from effectively recovering their data without resorting to paying ransom.
Throughout the webinar, we covered several essential topics that I believe are vital for all organizations to consider:
- Significant problems due to team collaboration gaps
- Risks imposed by departmental siloing
- Why and how to be prepared to restore production data
- The importance of building incident response capabilities
Let’s dive into each of them in greater detail.
Cybersecurity and Data Backup team’s collaboration gaps
Jason Buffington, talking about team’s not collaborating. Extracted from webinar.
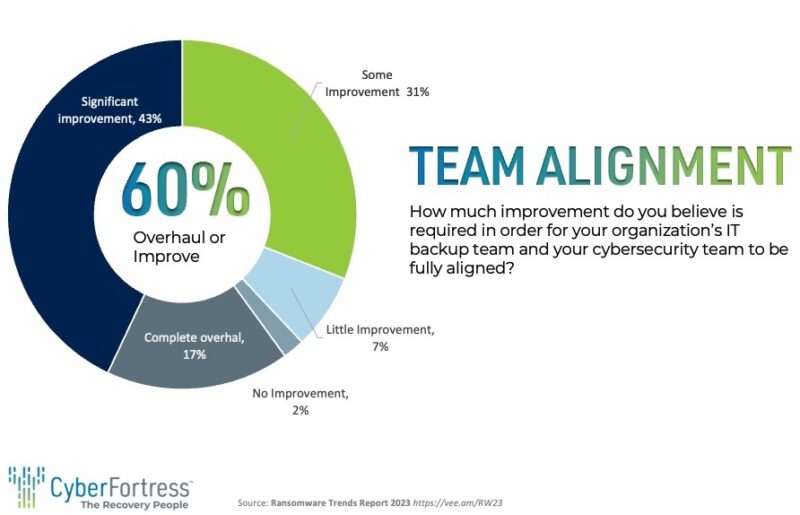
I have come across a significant finding from Veeam’s research that really struck a chord with me. The study highlighted the pressing need for enhanced collaboration within organizations, particularly between cybersecurity teams (often referred to as the “preparedness folks”) and backup teams (commonly known as the “remediation folks”). Out of the organizations surveyed, a staggering 60% expressed their desire for either a major improvement or a complete overhaul in the working relationship between these two crucial teams.
What personally resonated with me is how this finding reflects something I frequently encounter in my line of work.
When dealing with data protection and recovery efforts, we often find ourselves primarily interacting with the IT administrators who oversee the backups or conduct the tests. Occasionally, some of the more proactive ones may involve end users in the discussions, but it’s a rarity to witness the active participation of executives or the security team.
The exception seems to be when we’re dealing with environments that demand an exceptionally high level of security, like government offices.
This data only serves to emphasize the critical importance of fostering collaboration and communication among the various roles involved in cybersecurity and data protection efforts.
Bringing together cybersecurity teams and backup teams, along with executives and security personnel, is essential for a comprehensive and well-rounded approach to safeguarding valuable data. By breaking down the silos and encouraging open dialogue, we can bridge the gaps between different departments and work towards a more unified and effective cybersecurity strategy.
It’s evident that organizations must recognize the significance of this collaboration and actively implement measures to promote better working relationships.
Encouraging regular meetings, joint planning sessions, and knowledge-sharing initiatives can go a long way in maximizing the collective expertise and ensuring a robust defense against potential threats. As someone who is deeply committed to enhancing data protection and cybersecurity practices, I firmly believe that this kind of integrated approach is the key to success in today’s ever-evolving digital landscape.
Ransomware risks from departmental siloing
It’s been quite evident that there is a recurring pattern of limited communication and collaboration among various teams. It’s frustrating to see that different teams are often unaware of each other’s roles and responsibilities.
One major consequence of this lack of alignment among data backup and security teams is the inefficiencies it causes. Without proper communication and coordination, tasks are often duplicated, and valuable time and resources are wasted. What’s even more concerning is that this situation leaves us more vulnerable to cyber threats.
When teams are not on the same page, there are gaps in their defenses, which malicious actors can exploit.
During our disscusion one theme kept coming up again and again—the urgent need for better communication and breaking down these departmental silos.
To address this challenge, I personally feel that individuals need to take the initiative to reach out and engage with colleagues from other teams. It’s a small step, but it can lead to significant improvements in collaboration.
In conclusion, team alignment is not just an option; it’s a necessity for the success.
Importance of preparedness for disaster recovery
Cyber threats are now included in organizations’ broader disaster recovery strategies alongside traditional disasters like fire, flood, and natural calamities. And let me tell you, it’s not just something to brush aside lightly.
But how can you neutralize the threat of ransomware?
A reliable backup strategy was highlighted as a crucial foundation for any cybersecurity strategy. Testing the backups regularly was emphasized as a means to ensure their effectiveness and to mitigate and neutralize the potential impact of cyberattacks.
During the session, Jason brought up how ransomware can take everything down at once, but bringing the data back to operational doesn’t follow the same flow: While encryption technologies tend to operate in parallel, decryption technologies tend to operate in serial.
How does this affect my organization’s recovery point objectives?
Well, it means there’s no easy magic wand to wave and make everything work instantly and simultaneously. Unless we’re talking about unhardening a BIOS, most solutions will involve a step-by-step process that might take time, potentially causing significant loss in terms of productivity.
The important question you should ask yourself and take into consideration is: What’s the maximum amount of downtime our company can tolerate? If you don’t have an answer, it’s high time to start contemplating this question seriously and think about recovery time (and recovery point) objectives.
Here are some important numbers to keep in mind:
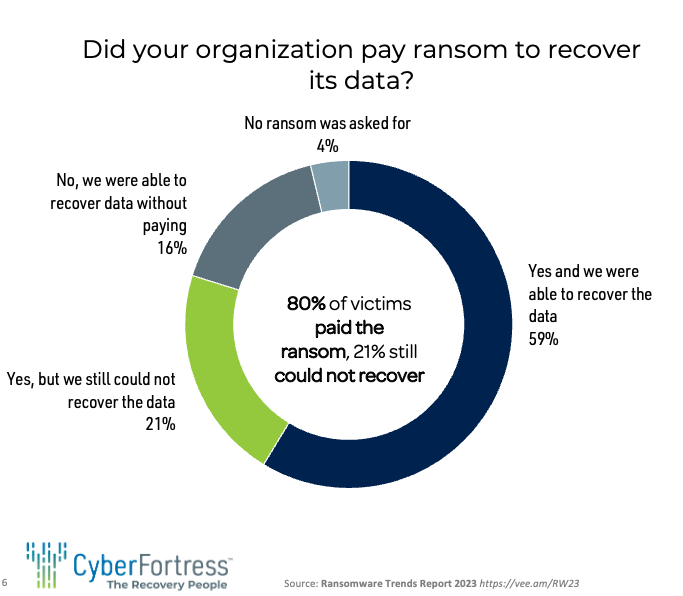
- One in four organizations that pay the ransom still couldn’t recover
- Twenty one percent paid but could not recover
- 45% of production data was affected by a cyber attack
These statistics serve as a stark reminder of the unpredictable and ruthless nature of ransomware attacks. It underscores the importance of adopting a proactive approach to cybersecurity and being prepared to face any eventuality.
Building ransomware incident response capabilities
No cybersecurity strategy is complete without a strong incident response plan. During our discussion, we stressed the significance of incident response teams and ransomware playbooks in effective cybersecurity practices.
While only a small percentage of organizations reported lacking these crucial components, there is a growing recognition across the board of their necessity. It is vital for organizations to document and update these plans regularly, ensuring their accessibility and usefulness during times of crisis.
By having a well-prepared ransomware incident response plan and building incident response capabilities, organizations can respond quickly and effectively to cyber threats. This will help mitigate their impact and enable the restoration of normal operations as smoothly as possible. Preparedness and documentation are the keys to ensuring the cybersecurity strategy’s success when facing challenging situations.
Being prepared to restore your data after ransomware
The need to be prepared for ransomware attacks, considering them a matter of “when” rather than “if.” The research data revealed that 85% of organizations surveyed experienced at least one cyber attack in a year.
The average number of attacks per year was 2.3. Furthermore, the survey highlighted the impact of these attacks, with an average of 45% of production data being affected or encrypted. This alarming statistic underscores the urgency of robust backup strategies and the importance of preparing for data restoration.
What kind of ransomware threats does CyberFortress’ Ransomware and Insider Protection (RIP), powered by Veeam protect against?
- Accidental backup deletion.
- Malware deletion of backups.
- Remote backup deletion by a malicious actor.
- Accidental Backup Deletion:
One of the primary challenges faced by businesses is the accidental deletion of critical backup data, leaving them vulnerable to data loss during a ransomware attack. Through a combination of intuitive user interfaces, permission settings, and monitoring mechanisms, RIP ensures that only authorized personnel can perform backup-related operations.
- Malware Deletion of Backups:
Ransomware attacks on businesses occur every 11 seconds. They shut down productivity, services, and revenue. Pay up and it’s still not likely you’ll get all your data back. Don’t panic, expired/deleted backups, intentional or malicious, move to CyberFortress repositories, repositories keep “deleted” data safe for a predetermined time with restricted employee access and removal only occurs when preset policy rules allow.
- Remote Backup Deletion by a Malicious Actor:
With the rise of sophisticated cybercriminals, businesses must prepare for the possibility of remote backup deletion carried out by malicious actors. Savvy attackers encrypt or delete your backup and archive data, leaving you nothing to recover. Consequences are crippling – damaging your reputation, operations, and bottom line. CyberFortress’ Ransomware and Insider Protection enables recovery from encrypted or deleted backups by providing an isolation layer.
To protect against malicious actors, it’s critical to get your data off of your domain with an immutable, air-gapped recycle bin that isolates the data for a pre-set policy period and to ensure security best practice – don’t forget to enable 2FA now available with Veeam’s Backup & Replication V12 upgrade.
Don’t let cyber criminals take your data hostage. Prepare to restore, embrace the reality of ransomware attacks, and prioritize robust backup strategies.


